Safe Computing Best Practices
Safe computing best practices are intended to help ensure the integrity of your computer and data. A few of these will be old news to some of you, but I feel that it is important to compile the list as a point of reference for our customers and blog readers.
-
Utilize Security Software
Antivirus software offers “real time protection” for downloads, email and suspicious website activity. This isn’t just a Windows problem either. People often think that Macs can’t get viruses. They’re wrong. Macs can and do get viruses, but at a substantially lower rate of occurrence than Windows machines. Install Heroes recommends Avast antivirus for Macs and PCs.
Your Mac and Windows based computers also include a basic firewall. It’s important to be sure this firewall is configured properly to be sure someone cannot access your data remotely.
-
Update Software
It’s important to keep your Operating System, Antivirus Software and all your other programs up to date. Out of date software is more likely to have vulnerabilities that can be exploited. It should be obvious that you need to keep your Antivirus software updated, but it’s equally important to keep your OS and other software updated as well. If hackers and malware creators find a way to exploit a program such as Adobe Reader or Microsoft Word and you don’t keep them up to date then your computer is at risk.
-
Create Stronger Passwords
Password management company SplashData has compiled a list of the top 25 most common passwords used in 2013. If your password is on the list it’s time to make a change. I suggest using a computer generated password. Norton has an online password generator which can assist with creating a random password. Random passwords are great because there is no chance someone is going to guess your password just because they know you. It’s also a bad idea to use the same password for every account. Once you have created a random password you can alter one or two characters for every different account. There are also a number of password management programs out there to assist with keeping track of which password goes with which account. Checkout Norton Identity Safe and RoboForm.
-
Backup!

Ensure your system is backed up regularly. Whether you perform manual backups with an external hard drive, rely on automatic backup software such as Acronis True Image or you backup to the cloud with a service like iDrive it’s important to be sure you have a backup plan in place. Having a backup will make your life much easier in the case of hard drive failure, virus attack or a lost/stolen computer.
A manual backup can be as simple as dragging and dropping documents from your computer onto a flash drive. It’s also important to have a backup of your Operating System. Gone are the days of getting a set of recovery discs with your new computer, now you’re responsible for creating them yourself. Most manufacturers include a utility to you help create these discs, but here are a couple of good tutorials for creating them in Windows 7 and Windows 8.
-
Be Weary Online
You should always be mindful of suspicious emails. Ignore unsolicited emails, and never click on attachments or links in emails if you don’t trust the source. Also be careful to notice if the URL of a link is going to the correct webpage. Simply hover over a link before clicking on it to see where it’s going to take you.
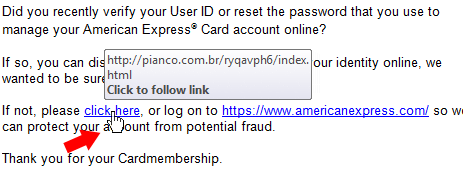
You should also be careful about where you go online. I suggest you stick with well known reputable websites and I also suggest you stick with a secure web browser such as Google Chrome. Checkout my post about web browsers and how to protect yourself from popups and malicious ads. -
Secure Disposal
When it’s time to upgrade to a new computer it’s time to think about how you are going to dispose of your old computer. Depending on how much personal data is on your computer you may be concerned about someone getting access to the information on your old computer. One method to ensure the integrity of your data is to remove the hard drive from your computer and keep it or physically destroy it with a shredding service.
Additionally, Install Heroes offers a consignment service where we will certify your computers hardware and list it for sale online. Many buyers are looking for parts computers or cheaper functional computers. We can almost always get something for your computer. And before we ship it out, we’ll be certain your hard drive is clean of all your personal data.
-
Limit Access
Whether you’re at home, work or out in public you should never leave your computer unattended when logged in. You should always lock or log off your computer when you step away. If a malicious stranger, pranking co-worker or unwitting child gets access to your computer and documents there’s no telling how much trouble it could cause for you.
-
Secure Your Router
It’s especially important to secure your wireless router and it’s important to only use secured connections when away from home. In a best case scenario you could be letting your neighbors mooch WiFi for free and thereby slowing down your connection. In a worst case scenario you could be opening yourself up to hackers and data thieves.
-
Free Software
There’s no such thing as a free lunch right? Well, that’s not so true with software, there is a lot of free software available for PCs and Macs. The problem is that there are a lot of untrustworthy freeware sites which may install rogue software on your computer. Mac users can checkout Get Mac Apps and Windows users can try Ninite.
Both sites allow you to check off all the software you wish to install, then you download a single file which seamlessly installs each program. The best part is that they also automatically opt out of all the junk programs and toolbars which often come with freeware programs.
-
Keep Informed
The best thing you can do to protect your computing experience is to stay up to date on security issues. Sites like Komando.com often have the newest online security news. You can also “Like” the Install Heroes facebook page and we’ll do our best to pass on the important security news as well as tips and tricks, hot deals, product reviews and general tech news.

 D5 Creation
D5 Creation
Comments are Closed